Cyber Security Review
Streamline Your Cyber Security Efforts with Toro's Comprehensive Review
Navigate the complexities of cybersecurity with Toro’s tailored cyber security review, ensuring your investments are precisely aligned with your most critical risks:
🔘 Targeted Risk Assessment: Identify and prioritise the vulnerabilities that could impact your operations through Toro's cyber security review.
🔘 Strategic Roadmap Development: Receive a customised action plan that guides your future security investments and remediation efforts.
🔘 Regulatory Compliance and Optimisation: Meet compliance standards and optimise your security spending based on informed insights.
Take the first step towards smarter cyber security management.
Request Your cyber security Review Consultation now...
Our Approach
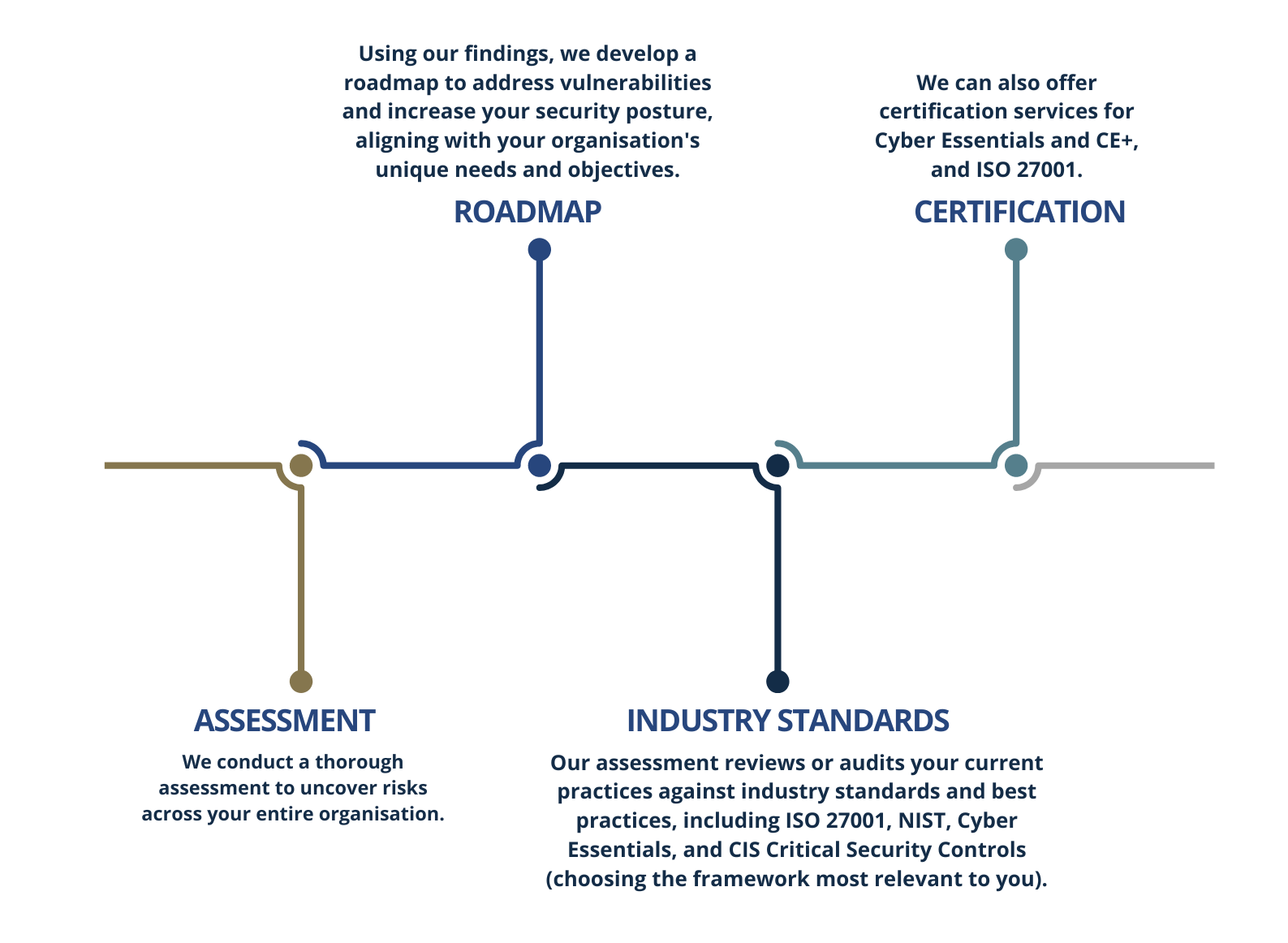
Why should you conduct a review?
Reassure Customers

A comprehensive cyber security review demonstrates best practice and helps create organisation-wide security culture that reassures customers, investors, and partners that their reputation, information, and assets are in safe hands.
Winning & Enabling Business

By managing risk exposure more effectively, you will demonstrate a tender-winning ‘differentiator’ over less mature competitors.
Avoid a Security Breach

By understanding risks and supporting the development of continual security improvement, you’ll reduce the likelihood and impact of a damaging cyber-attack.
Security Optimisation

Understanding what attack pathways to critical activities must be ‘hardened,’ you'll optimise security resources and prioritise spend.
Cost Effective Risk Management

By better understanding threats, vulnerabilities, and risks, you will be better placed to develop pragmatic business resilience and an effective disaster recovery plan.
Regulatory Compliance

Demonstrate third party assurance and documentary evidence that prevents the reputational and financial impact of compliance failure.
Why Toro?
Attackers exploit vulnerabilities across cyber, physical, and human domains to infiltrate organisations. Toro’s approach to cyber security reviews is comprehensive and adaptive, delivered with a blended approach to security in mind.
Over the past five years, we've conducted cyber security reviews for 100’s of critical suppliers to UK Government departments and our extensive experience spans from assisting NGOs with cost-effective solutions to collaborating with enterprise-level entities with substantial budgets and diverse needs.
We provide MSP services, so when it comes to reviewing yours, we understand how they work and any restraints they might face. We also offer incident response support, so we can offer practical insights into potential threats facing your business.
If you want support in achieving a certification at the end of the cyber security review, we can support you e.g. Cyber Essentials, Cyber Essentials Plus or ISO 27001. Our unique position allows us to guide you in improving your security measures, support you in implementing changes, all whilst safeguarding the long-term future of your business.
FAQs
Should we implement a security framework?
Cyber security frameworks offer a good blueprint for your organisation. The first part of improving cyber security is understanding your current position and having a framework that can give you a standard, industry recognised approach to baseline and build a roadmap for improvement.
What does a cyber security review include?
A cyber security reviews involves a thorough examination of your organisation’s systems, processes, and policies. It includes identifying potential vulnerabilities, assessing existing security controls, evaluating compliance, and providing recommendations for improvements.
How long does a cyber security review take?
This depends on several factors including the size and complexity of your organisation, and availability of key business stakeholders.
What happens after a cyber security review is completed?
You’ll receive a detailed report, outlining findings, recommendations, and a roadmap for improvement. We can then support you to implement the suggested improvements, help you monitor progress and provide ongoing support.
What is ISO 27001?
ISO 27001 is an international standard for information security management. In short, ISO 27001 is a set of standards for managing risk related to information security. It covers policies, procedures, training, monitoring, auditing, incident response, and communications.
How often is ISO 27001 certifications renewed?
ISO 27001 certification is valid for three years, but you are expected to receive a surveillance audit annually. Every three years you will need to undergo a recertification audit to maintain your certification. In addition to the surveillance and recertification audits, you will be required to conduct regular internal audits and management reviews to ensure ongoing compliance with ISO 27001 requirements.
How long does it take for ISO 27001 to be implemented?
The timeline for implementing ISO 27001 varies depending on factors such as the size and complexity of your organization, existing security measures, and resources allocated to the project. On average, implementation takes 6 – 12 months.
What’s the difference between a cyber security review and cyber security audit?
A cyber security audit confirms the presence of specific security controls at a point in time, while a cyber security review provides a thorough assessment of these controls, consider their effectiveness, and evaluates an organisation's overall cyber maturity.
Which should we start first: Cyber Essentials, ISO 27001, or both at the same time?
If you are able, it will be more efficient to start both at the same time – Toro can support with this. However, if you are limited on resources, time commitments and budget, you could start with the Cyber Essentials and then continue to ISO 27001 when you are ready.
Why is a Cyber Security Review important?
A Cyber Security Review is essential for understanding your organisation's current security posture and identifying areas for improvement. It helps pinpoint vulnerabilities, assess risks, and establish a clear roadmap for enhancing your defences. Regularly conducting one ensures your organisation is prepared to address evolving threats and comply with industry regulations. This proactive approach reduces the likelihood of security breaches, protecting your reputation and assets.
Is a Cyber Security Review suitable for small businesses?
Yes, it's valuable for organisations of all sizes, including small businesses. Smaller organisations are increasingly targeted by cybercriminals due to perceived weaker defences. A Cyber Security Review provides an affordable and scalable way to identify risks, strengthen security measures, and align with best practices like Cyber Essentials or ISO 27001. It’s a proactive step to safeguard your business, no matter its size.
How often should a Cyber Security Review be conducted?
The frequency depends on the size and nature of your organisation, as well as the evolving threat landscape. As a best practice, it’s recommended to conduct a Cyber Security Review annually or after significant changes, such as adopting new technologies or experiencing a security incident. Regular reviews ensure your defences remain effective and aligned with the latest threats and compliance requirements.
